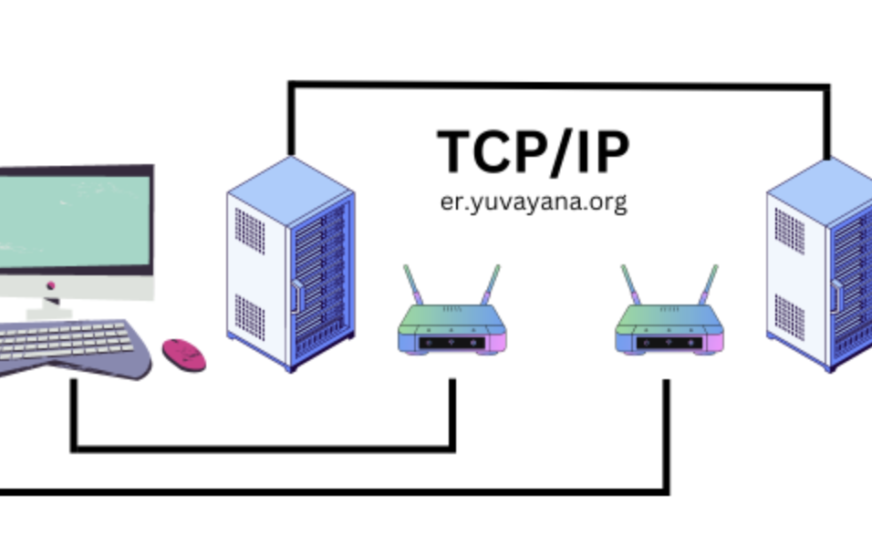
TCP/IP Protocol
Let’s start with an overview of the OSI reference model. The OSI model has seven layers: application, presentation, session, transport, network, data link, and physical. Now, let’s compare these with the layers of the TCP/IP model, which has four layers: network access, internet, transport, and application. The TCP/IP model was
Blockchain Technology: A Comprehensive Overview and How It Works
Blockchain technology is a distributed database that enables secure, transparent, and tamper-proof record-keeping. It’s ideal for a variety of applications, ranging from financial services to supply chain management. In simple terms, blockchain is a digital ledger that stores data across multiple computers globally, meaning it’s not limited to just one
Implementing and Preventing DoS Attacks on Ubuntu
Understanding DoS and DDoS Attacks: Implementation and Prevention on Ubuntu Introduction A Denial-of-Service (DoS) attack occurs when an attacker makes a network or system unavailable to users, either temporarily or indefinitely. A Distributed Denial-of-Service (DDoS) attack, on the other hand, utilizes multiple systems to overwhelm a target. Both types of
Types of Network Connections
Let’s explore the different types of networks, many of which people are familiar with, but there are several other types that might not be as well-known. Personal Area Network (PAN) A PAN is a small network used for personal purposes. It connects devices like tablets, laptops, and smartphones, usually through
The Boundary Between Hardware and Software in Computing
Cloud computing has become increasingly popular and is likely to continue growing. Its appeal comes from the many advantages it offers, especially for those who make the switch. Cloud computing provides far more storage than traditional physical devices, making data management, sharing, and availability much easier. Today, we use cloud-based
Surviving the Data Crisis: Must-Have Data Backup Tools for Small Businesses
Surviving a Data Crisis: Essential Data Backup Tools for Small Businesses Imagine this: the alarms go off, a flickering light bulb sways overhead, and chaos erupts around you. Papers are scattered, colleagues are in distress, and there’s a sense of panic in the air. No, it’s not the apocalypse –
Understanding the Difference Between Basic and Dynamic Hard Disks
Your hard drive is where your files and operating system are stored, and without it, you can’t really use your computer—unless you’re booting from a CD or USB flash drive temporarily. “Disk” is another term for a hard drive, and there are different types of disks that work with the
Steganography
Introduction to Steganography In this discussion, we’ll explore the basics and limitations of steganography, as well as highlight the differences between steganography and cryptography. What is Steganography? Steganography is the practice of hiding a message within another form of content. Unlike encryption, which scrambles the message to make it unreadable,
An Introduction to Database Management Systems
Introduction to Database Management Systems Today, every company collects and processes vast amounts of data. To manage this data efficiently, businesses rely on database systems. Take Flipkart, for example. It gathers huge volumes of data and uses a database system to store, organize, and leverage this data. So, what exactly
How to Seamlessly Sync Microsoft OneDrive and Dropbox
Cloud Computing and Smart Sync In today’s world, everything is connected through the internet, and data has become one of the most valuable assets. People want to store their data securely and access it from anywhere. This is where cloud computing comes in, offering a modern way of storing data